Ransomware making headlines may seem like the norm these days, but for businesses and security teams, it’s a serious, daily reality. Each new tactic reveals a little more about how these attackers operate—and offers a chance to strengthen our defenses. By analyzing ransomware activity from September, we’ve uncovered new patterns in how cybercriminals target victims and industries.
Our deep dive into the numbers reveals 434 victims claimed by ransomware groups during this period, each one a reminder that the fight against cybercrime is far from over.
Now, Let’s explore the most notable ransomware news and findings since our last edition:
- Operation Chronos Disrupts Evil Corp Campaigns: Evil Corp, a group with ties to the Kremlin, deployed Dridex and REvil throughout their ransomware-as-a-service (RaaS) campaigns. They also used LockBit ransomware with the assistance of a LockBit affiliate. A takedown by law enforcement resulted in the identification of more than 25 Evil Corp staff, comprised of members, facilitators, and other supporters. More than four LockBit affiliate members were arrested, including a LockBit leader and developer. One of the authorities tasked with the investigation, the National Crime Agency (NCA), concluded that the LockBit 3,0 ransomware does not result in the deletion of victim data.
- DragonForce Operations Employ LockBit and Conti Variants: DragonForce leverages modified tools in their ransomware attacks. They have executed payloads containing customized elements of LockBit and Contiv3. DragonForce also deploys tools such as the backdoor SystemBC and Cobalt Strike. Affiliate members who support DragonForce may receive 80% of the profits gained in their RaaS operations.
- Cicada Continues to Hit VMWare ESXi Environments: Cicada3301 ransomware attacks impact VMWare ESXI environments on both Windows and Linux hosts. This ransomware’s connection to another RaaS group, ALPHV, and the distributor Repellent Scorpius have seen significant developments.
- CosmicBeetle Joins Forces with RansomHub: CosmicBeetle or NONAME, operates as an affiliate of RansomHub. CosmicBeetle was once known for using malicious tools like Spacecolon and executing payloads that ran the Scarab ransomware; however, they now use Scransom and RansomHub CosmicBeetle has launched attacks against organizations in Europe and Asia across manufacturing, technology, finance, and health and science sectors.
- RansomHub Implements Another Defense Evasion Tactic: RansomHub, a group that previously used EDRKillShifter, has adopted a different method to stop EDR services. The group has recently used a legitimate service called TDSSKiller. The tool interacts with kernel-level processes once run, e.g., through the execution of a batch file; RansomHub uses TDSSKiller to identify and terminate active EDR services.
- Critical SonicWall Flaw Exploited By Ransomware Groups: CVE-2024-40766 is a security flaw that affects SonicWall Gen 5, Gen 6, and Gen 7 devices with SonicOS 7.0.1-5035 and older OS iterations. The vulnerability results in unauthorized access to the affected system and may cause the firewall to crash; Akira is one of the larger ransomware groups that has exploited this flaw to perform remote code execution. Organizations with products impacted by this vulnerability are advised to disable the WAN management functionality enabled over the Internet on the firewall and SSL-VPN service, restrict access to trusted users and devices, and enforce MFA.
- Russian Cryptocurrency Exchanges Subject to Sanctions: The United States Treasury’s Office of Foreign Assets Control recognized that Russian gangs and ransomware groups were engaging in money laundering activities. These organizations exchanged virtual currency and accrued financial assets in the millions. As a result, the U.S. Treasury imposed sanctions on Cryptex and PM2BTC, two prominent Russian cryptocurrency exchanges, to freeze assets accessed by criminals, prevent the flow of assets from illicit transactions to foreign institutions, and elicit the support of law enforcement to investigate any parties involved.
- FBI Takedown Disrupts Marketplace Run By Russian/Kazakh Criminals: An FBI-led operation dismantled the WWH Club marketplace. The marketplace was used to sell stolen information and other resources to criminal syndicates, such as tools to launch cyberattacks and information to commit fraud and evade law enforcement.
- INC Ransomware Strain Attacks Healthcare Systems: The distribution of an INC ransomware variant has resulted in attacks against the healthcare industry. The main threat actors involved in these operations are Vanilla Tempest and Storm-0494. The groups likely purchased the INC ransomware code from the threat actor salfetka. The common attack vectors exploited in these attacks include public facing services connected to the Internet, unpatched systems, and retaining default privilehged credentials.
- New Ransomware Group, Valencia: Valencia ransomware has claimed several victims in the month of September, exfiltrating data such as PII and other sensitive infromation. The group operates a data leak site and may have connections to a hacking persona known as LoadingQ.
- Threat Actors Exploit AD Tools to Exfiltrate Data: Azure Storage Explorer and the command line utility AzCopy are AD cloud-integrated tools that allow a user to transfer data and manage storage resources. The ransomware groups BianLian and Rhysida install the tools in victim environments to upload data to blob storage. The use of a tool like Azure Storage Explorer is advantageous for the threat actor because they can upload a large volume of data; the odds of prompt detection may also be reduced since the threat actor is using a service that has a Microsoft IP address.
Top 10 Ransomware Families
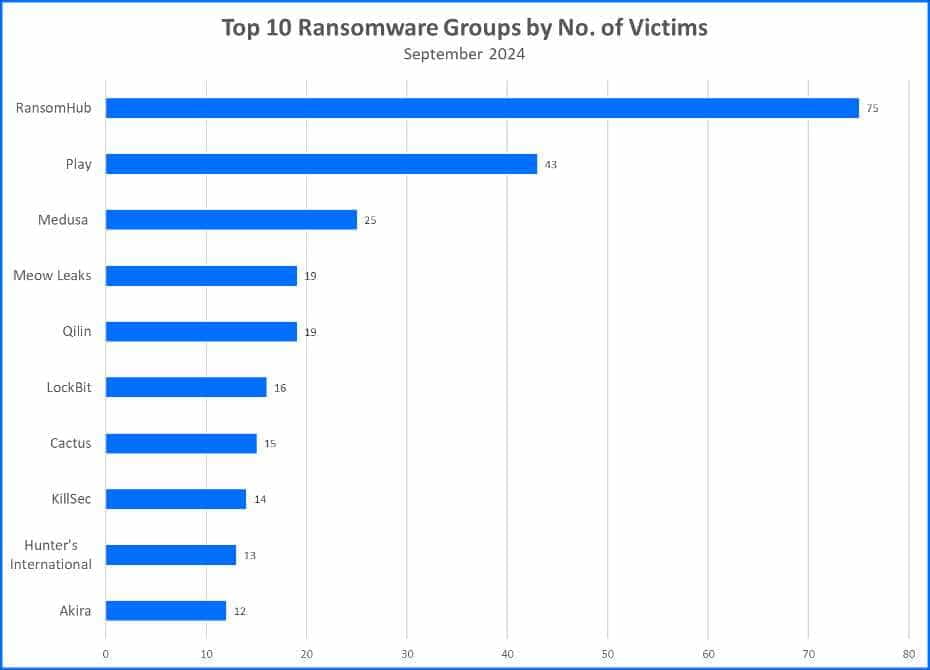
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where attacker groups publicize their claimed number of compromised companies. This approach provides valuable insights into the overall activity of the RaaS market. However, there's a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and might be unreliable. Additionally, this method only captures the number of claimed victims, not the actual financial impact of these attacks.
Top 10 Countries
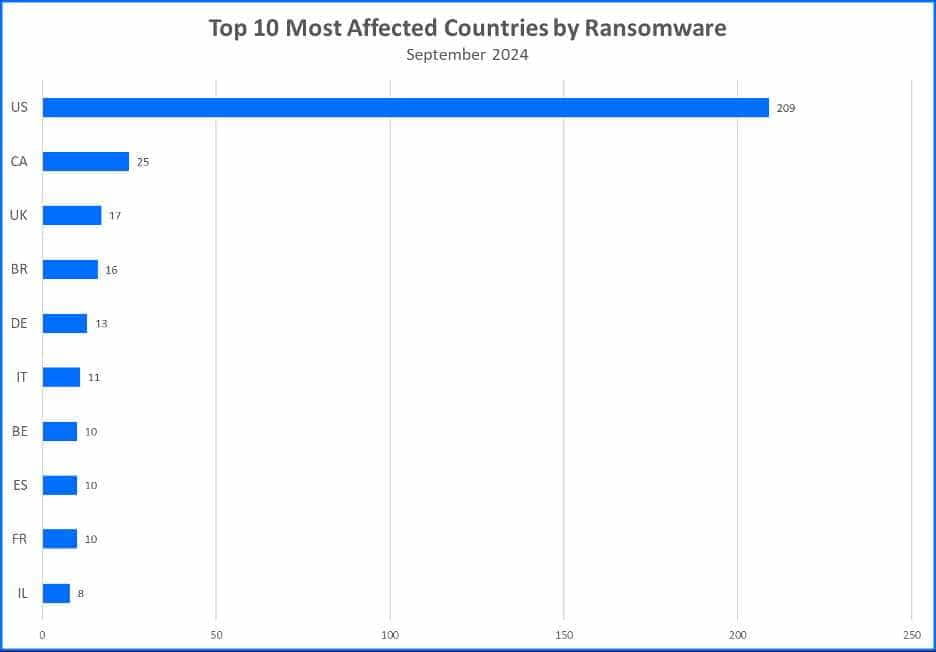
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
Read More
#Bitdefender #Bitdefender Threat Debrief #cybersecurity #ransomware attacks #cybercriminals #NetMon
