On the 5th of August, Bitdefender rolled out new functionality in Bitdefender GravityZone, a comprehensive cybersecurity platform that provides prevention, protection, detection, and response capabilities for organizations of all sizes. These features, consistent with our multi-layered security strategy, are intended to ease the workload of security analysts, administrators, and users.


What’s new for Security Analysts
In a dynamic cybersecurity landscape, security analysts are responsible for uncovering any signs of potential sophisticated attacks to make the invisible visible. This section describes new functionality designed to elevate the capabilities of analysts, offering enhanced tools for threat detection, investigation, and response.
Monitor Multiple Subnets with a Single Network Sensor
Sensors in Bitdefender GravityZone actively monitors your IT infrastructure like devices, networks, cloud, identities, and productivity applications for potential threats, including ransomware attacks. Network Sensor specifically analyzes network traffic to detect and prevent lateral movement, data exfiltration, port scanning, and brute-force attacks, providing crucial insights into network-based threats.
With the latest update, you can monitor multiple network subnets using a single Network Sensor Virtual Appliance. You can now configure multiple VLANs for monitoring, and by adding network router definitions for your networks, the sensor and correlation engine can better understand network topology and traffic flow. To prevent IP and MAC address conflicts caused by subnets with overlapping address spaces, you can define Group IDs to logically partition your network infrastructure, thereby ensuring that detections from such networks are differentiated and accurately marked.
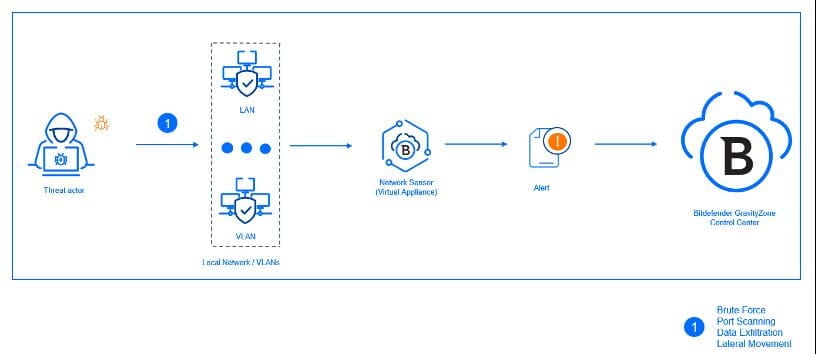
This new functionality will be available automatically on your existing network sensors. However, to benefit from these improvements, existing customers will need to reconfigure their existing virtual appliances. All configuration steps are described in detail on our Bitdefender support center here.
What’s new for Administrators
With administrators constantly juggling numerous tasks and responsibilities, tools designed to make their daily tasks easier are highly appreciated. This section describes new functionality designed to facilitate the management of features responsible for prevention, protection, and detection in a defense-in-depth security architecture.
Automatic Response for Custom Rules
Until now, you could use custom detection rules to define rules that mark specific behavior (custom IoC) from your environment as a valid detection and generate corresponding incidents on the Incidents page.
With the latest release you can assign automatic actions for custom detection rules. Depending on your license, you can set the following response actions:
* Isolate – it isolates the endpoint where the detection occurred.
* Collect investigation package – collects relevant data and logs from the system where detection occurred. The package will be stored locally on the endpoint side and can be downloaded using the retrieve file option in the Investigation section under the endpoint detail.
* Add to Sandbox – send the file that triggered the detection to Sandbox Analyzer.
* Kill Process – terminate the process that triggered the detection. You can choose to include parent process and child processes.
* Antimalware scan – run on-demand scan on the endpoint that triggered the detection. You can choose between a quick and full scan.
* Quarantine – quarantine the file or process that triggered the detection. You can choose to include parent process and files or child processes.
* Risk scan – run risk scan on the endpoint that triggered the detection.
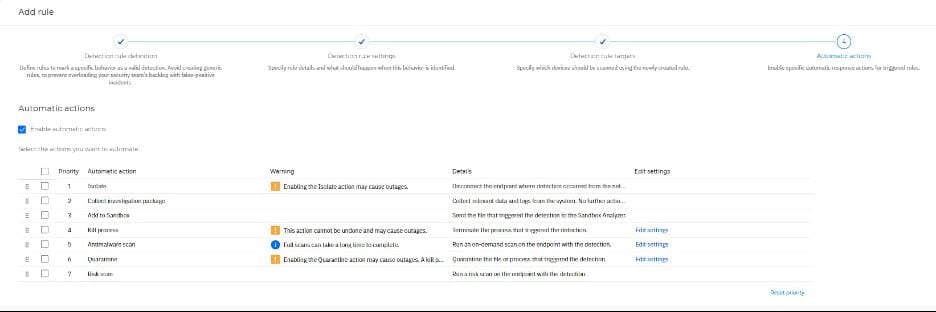

You can choose one or multiple actions and define their priority by dragging and dropping the automatic actions from top to bottom. This will determine the action execution order, with actions being executed sequentially one after another, without waiting for the results of the previous one. Actions will be executed during detection without any dependence on endpoint connectivity to GravityZone Cloud.
For example, after reading our analysis about a coordinated ransomware attack on corporate networks made by the Cactus ransomware group, you can create your own custom detection rules based on the IoC provided in the article. By using C2 IP addresses, you can create a rule where, after detection, the compromised host will be isolated, an investigation package created, and antimalware and risk scans executed.
All configurations are logged and available for review with full details in the User Activity section. All actions will be reported and displayed in GravityZone Incident section with complete details.
New Blocklist Rules
Using GravityZone, you can block applications based on application control in the Content Control policy and block traffic based on the Firewall Policy. With an EDR subscription, you have the additional ability to block applications based on hash in the Blocklist section under Incidents.
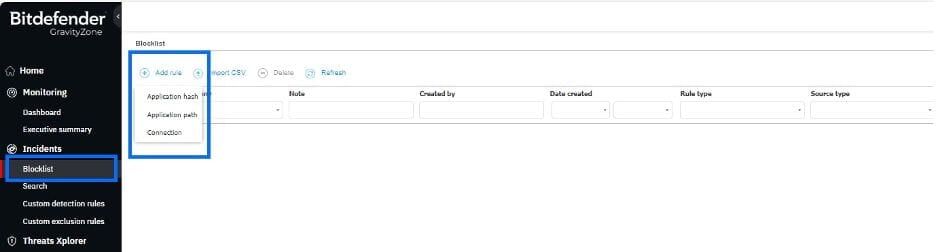
We have enhanced the Blocklist with the latest update by adding path-based application blocking and connection blocking. In addition to existing hash rules, you can now add blocks based on application paths. This feature works on Windows endpoints where both the Content Control and Application Blacklisting module are active within the Policy configuration. To configure new connection blocks with a deny action, the Firewall module must be installed and active on Windows endpoints. All the configuration changes are logged and available to review under the User Activity section.
It is important to note that all Blocklist rules are applied before Policy settings such as Content Control or Firewall configuration. All endpoints meeting the requirements outlined in the previous paragraph will automatically begin applying these rules.
You can also import local CSV files to easily add many rules at once or automate your task with the latest version of the API released for bulk rule creation.
Advanced Threat Control Enhancements
Advanced Threat Control proactively and dynamically detects malicious behavior by continuously monitoring process activities in real-time.
Sensitive Registry Protection, an existing component of ATC, has been enhanced to safeguard critical registry keys, including those associated with the Security Account Manager (SAM), from unauthorized access or exploitation via Windows Remote Registry Protocol (MS-RRP), which is used to remotely manage the Windows registry.
To illustrate, let's imagine an unprotected machine with unauthorized access. The SAM registry stores hashed passwords for local user accounts. Attackers can use exploitation techniques like malicious registry key dumping to extract the SAM registry and then attempt to crack the hashed passwords. Armed with valid credentials, an attacker could try to connect to another remote machine using MS-RRP and retrieve its SAM keys. If ATC is active on the remote machine with the Kill Process action, it will terminate the process (svchost.exe) that attempts to access the registry.
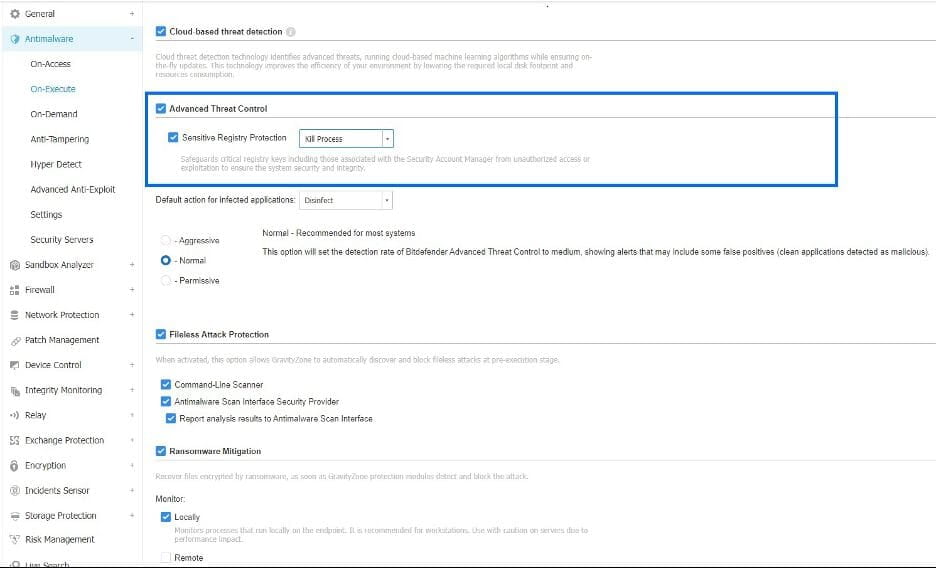
You can configure either Kill Process or Report Only for each new or existing Policy under Antimalware > On-Execute > Advanced Threat Control configuration section.
New Sandbox Analyzer Submission Task
Sandbox Analyzer service analyzes suspicious files in depth by detonating payloads in a contained virtual environment hosted by Bitdefender, observing their behavior, reporting subtle system changes that indicate malicious intent, and providing actionable insight.
With the latest release you can submit files to Sandbox Analyzer directly from Network section using Submit to Sandbox Analyzer Task.

Specify the exact location of the file(s) you wish to detonate. You can select up to five files per attempt. For added control, you can choose to run specific commands to be executed when the detonation starts.
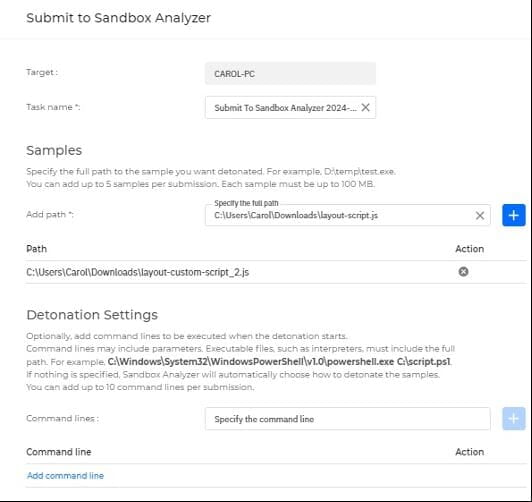

All submission tasks are logged in the User Activity section with details such as who created the task, what paths were added, when it was created, and what commands (if any) were mentioned in the task. The sandbox analysis report is available only in the Sandbox Analyzer section.
Introducing the New Network Section in GravityZone
Starting with the policy configuration redesign delivered last month, we are excited to introduce a new Network section in the GravityZone console interface. Once you enroll in the Early Access Program, you can find this redesigned section in the main GravityZone menu, labeled as EA Network. The previously used Network section will remain available to you during this transition period.
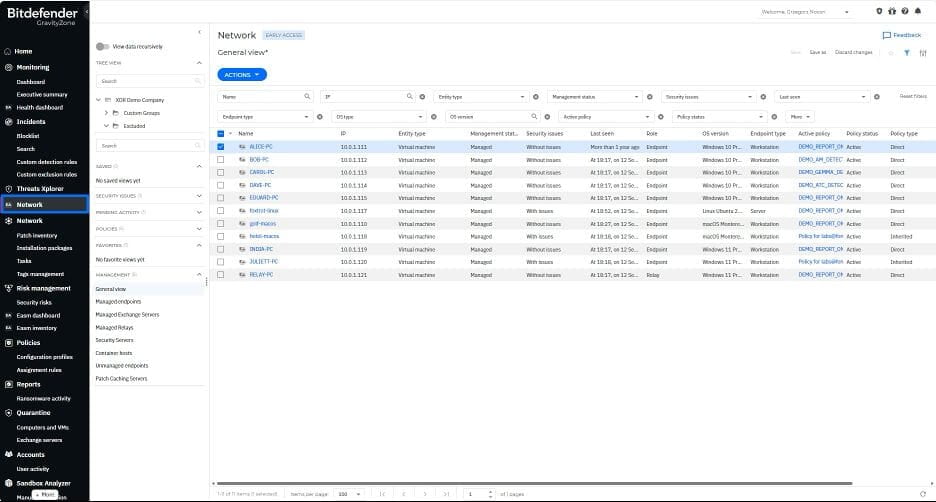
With a new Network interface, you can efficiently monitor endpoint status, allocate resources, and resolve issues. This update features graphical elements such as icons representing companies, virtual and physical machines, containers as well as a redesigned tree view with new filters and search options. We have also created several default smart views based on specific filtering rules for device discovery.
Summary
Bitdefender GravityZone platform stands out from the crowd, offering a one-stop solution for all your organization's security needs. As the digital landscape evolves, Bitdefender remains proactive, providing prevention, protection, detection, and response capabilities, ensuring the ongoing safety of organizations of all sizes worldwide.
To learn more about the Bitdefender GravityZone platform, contact us for more information. You can also start a free trial by requesting a demo here.
Author: Grzegorz Nocoń, Technical Marketing Manager, Bitdefender
Read More
#Bitdefender #Bitdefender GravityZone #cybersecurity #cybersecurity #Network Sensor #EDR #NetMon
